Read Access Is Allowed From Event Dispatch Thread or Inside Read-action Only
If you cannot open up or map network shared folders on your NAS, Samba Linux server, computers with legacy Windows versions (Windows 7/XP/Server 2003) from Windows ten or 11, most probable the trouble is that legacy and insecure versions of the SMB protocol are disabled in the current Windows builds (SMB protocol is used in Windows to admission shared network folders and files).
Microsoft is systematically disabling legacy and insecure versions of the SMB protocol in all recent versions of Windows. Starting with Windows 10 1709 and Windows Server 2019 (both in Datacenter and Standard editions), the unsafe SMBv1 protocol is disabled by default as well every bit anonymous (guest) access to network shared folders.
The specific steps to take depend on the mistake that appears in Windows when accessing a shared folder, and on the settings of the remote SMB server that hosts the network shares.
Contents:
- Tin't Access Shared Folder Considering Security Policies Block Unauthenticated Guest Access
- Can't Connect to the File Share Considering Information technology's Not Secure and Requires the Obsolete SMB1 Protocol
- Windows Cannot Access Shared Folder: You Don't Have Permissions
- Other Fixes: Windows Cannot Access Shared Folders
Tin't Access Shared Folder Because Security Policies Block Unauthenticated Guest Admission
Starting with Windows x build 1709 Fall Creators Update (Enterprise and Education editions), users began to complain that when they tried to open up a network shared folder on a neighboring computer, an fault appeared:
Restoring Network Connections An error occurs when you try to open a network binder: An fault occurred while reconnecting Y: to \\nas1\share Microsoft Windows Network: You tin't access this shared folder considering your organization'southward security policies cake unauthenticated invitee admission. These policies help protect your PC from unsafe or malicious devices on the network.
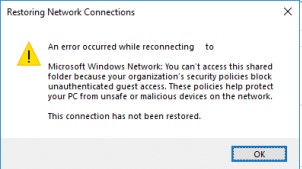
Moreover, on other computers with Windows 8.1, Windows seven, or Windows x with a build of upwards to 1709, the same shared network folders open normally. The point is that in modernistic versions of Windows ten (build 1709+), the guest access to the shared folders using the SMBv2 protocol is disabled by default. Invitee (anonymous) means access to a shared network folder without hallmark. When accessing a network binder under a invitee account over the SMBv1/v2 protocol, such methods of traffic protection as SMB signing and encryption are not used, which makes your session vulnerable to the MiTM (human being-in-the-eye) attacks.
These changes are not applied on Windows 10 Dwelling editions and the network admission under the guest account is working fine.
If you endeavour to open a shared network folder using the SMB v2 protocol under the guest business relationship, the following error will appear in the Event Viewer of your computer (SMB client):
Log Proper name: Microsoft-Windows-SmbClient/Security Source: Microsoft-Windows-SMBClient Consequence ID: 31017 Rejected an insecure guest logon.
This error says that your computer (client) blocks non-authenticated access under the Invitee account.
In nigh cases, you can confront this trouble when accessing sometime NAS devices (usually guest admission is enabled on them for ease of setup) or when opening shared folders on legacy Windows 7/2008 R2/Windows XP/2003 devices with anonymous (invitee) access enabled (run into the table of supported SMB protocol versions in unlike Windows editions).
Microsoft recommends irresolute the settings on a remote estimator or NAS device that hosts the shared network folders. It is appropriate to switch the network share to the SMBv3 mode. Or configure access with hallmark if only the SMBv2 protocol is supported by the device. This is the almost correct and safest fashion to gear up the problem.
Disable invitee access on the device where your shared folders are stored:
- NAS devices – disable invitee access in the settings of your NAS device (depending on vendor and model);
- Samba server on Linux — if you lot are sharing a network folder with Samba on Linux, add the following string to the smb.conf configuration file under the section [global]:
map to invitee = never
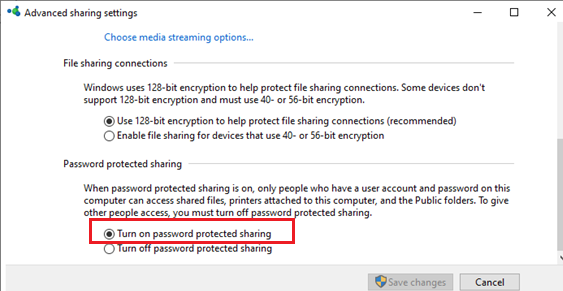
And restrict anonymous access in the shared folder configuration section:invitee ok = no - In Windows, you tin enable sharing of network folders and printers with password protection via the Command Console -> Network and Sharing Middle -> Advanced sharing settings. For All Networks in the "Password Protected Sharing" section, change the value to the "Plow on password protected sharing". In this instance, bearding (guest) access to the network shared folders volition be disabled and you will have to create local users, grant them admission permissions to the shared folders and printers and use these accounts to connect to the shared folders on a remote figurer.
There is another way – you can change the settings on your Windows device to allow access to shared network folders under the invitee account. This method should be used only as a temporary workaround (!!!), because admission to folders without authentication significantly reduces your reckoner security.
To enable guest access from your figurer, you demand to apply the Group Policy Editor (gpedit.msc). Become to the department: Computer Configuration -> Administrative templates -> Network -> Lanman Workstation. Discover and enable the policy Enable insecure guest logons.This policy option determines whether the SMB client will allow an dangerous guest logon to the SMB server.
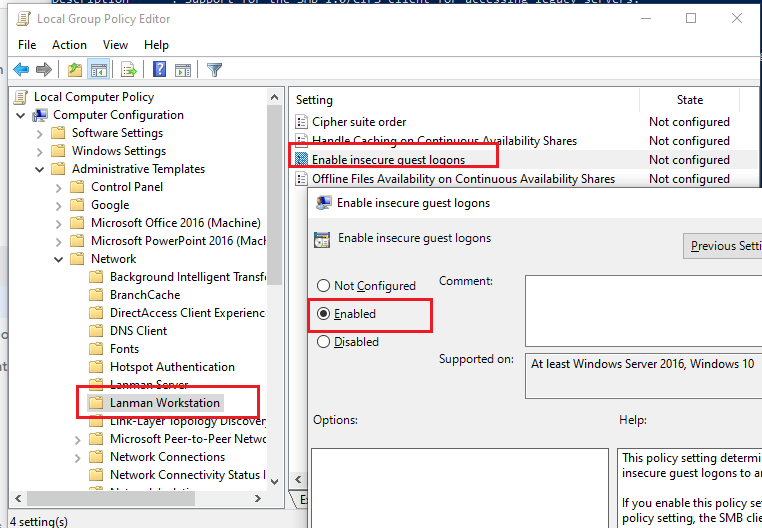
Update the Group Policy settings in Windows with the command:
gpupdate /force
In Windows x Abode, which does not have a local GPO editor, y'all can make a similar modify through the Registry Editor manually:
HKLM\SYSTEM\CurrentControlSet\Services\LanmanWorkstation\Parameters "AllowInsecureGuestAuth"=dword:1
Or with these commands:
reg add HKLM\Arrangement\CurrentControlSet\Services\LanmanWorkstation\Parameters /v AllowInsecureGuestAuth /t reg_dword /d 00000001 /f
reg add HKLM\Software\Policies\Microsoft\Windows\LanmanWorkstation /5 AllowInsecureGuestAuth /t reg_dword /d 00000001 /f
Tin't Connect to the File Share Considering It's Not Secure and Requires the Obsolete SMB1 Protocol
Another possible trouble when accessing a network folder from Windows 10 is that just the SMBv1 protocol version is supported on the server-side. Since the SMBv1 client is disabled by default in Windows 10 1709+ when you try to open the shared folder or map a network drive, you may go an fault:
You can't connect to the file share considering it's non secure. This share requires the obsolete SMB1 protocol, which is unsafe and could expose your organisation to attack. Your system requires SMB2 or higher.
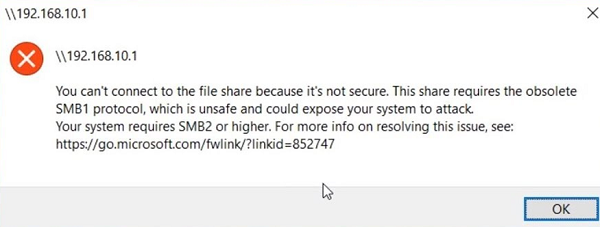
The error message clearly shows that the network shared folder only supports the SMBv1 customer access protocol. In this instance, you should try to reconfigure the remote SMB device to use at least SMBv2 (the correct and prophylactic way).
If you utilize Samba server on Linux to share files, y'all can specify the minimum supported version of SMB protocol in the smb.conf file similar this:
[global] server min protocol = SMB2_10 client max protocol = SMB3 client min protocol = SMB2_10 encrypt passwords = true restrict anonymous = 2
On Windows vii/Windows Server 2008 R2, you can disable the SMB i protocol and enable SMBv2 through the registry with the following PowerShell commands:
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Blazon DWORD -Value 0 –Force
Set-ItemProperty -Path "HKLM:\System\CurrentControlSet\Services\LanmanServer\Parameters" SMB2 -Blazon DWORD -Value one –Force
On Windows viii.i/Windows Server 2012 R2, y'all can disable SMBv1, let SMBv2 and SMBv3 with the post-obit command (verify that a private or domain contour is used for your network connectedness):
Disable-WindowsOptionalFeature -Online -FeatureName "SMB1Protocol"
Set-SmbServerConfiguration –EnableSMB2Protocol $true
If your network device (NAS, Windows XP, Windows Server 2003) supports just the SMB1 protocol, you tin can enable a carve up SMB1Protocol-Customer feature on Windows 10/11 or Windows Server. Just this is not recommended!!!
If the remote device requires SMBv1 to connect, and this protocol is disabled on your Windows device, an fault appears in the Event Viewer:
Log Proper noun: Microsoft-Windows-SmbClient/Security Source: Microsoft-Windows-SMBClient Consequence ID: 32000 Clarification: SMB1 negotiate response received from a remote device when SMB1 cannot exist negotiated by the local estimator.
Run the elevated PowerShell prompt and verify that the SMB1Protocol-Client is disabled (State: Disabled):
Get-WindowsOptionalFeature -Online -FeatureName SMB1Protocol-Client
Enable the SMBv1 client protocol (a reboot is required):
Enable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol-Customer
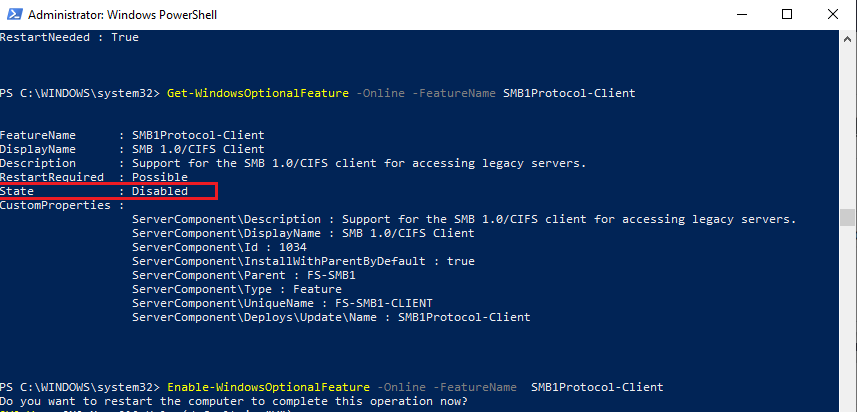
You can also enable/disable additional features in Windows 10 and 11 from the optionalfeatures.exe. Expand SMB 1.0/CIFS File Sharing Support and enable the SMB 1.0/CIFS Client.
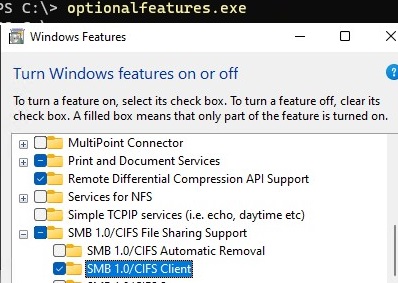
On Windows x 1809 and newer, the SMBv1 customer is automatically removed if it has non been used for more than 15 days (the SMB 1.0/CIFS Automatic Removal component is responsible for this).
In this case, I enabled but the SMBv1 customer. Do not enable the SMB1Protocol-Server feature if your computer is non used by legacy clients equally an SMB server to host shared folders.
After installing the SMBv1 client, you lot should be able to connect to a shared folder or printer without any issues. However, you should understand this workaround is non recommended, because it reduces the security of your computer.
Windows Cannot Access Shared Folder: You Don't Take Permissions
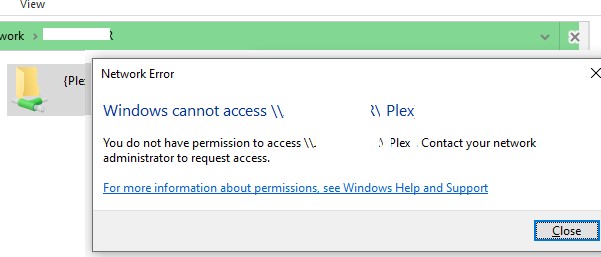
When connecting to a shared network binder on a remote computer, an error may appear:
Network Error Windows cannot admission \\PC12\Share Y'all practice not have permission to admission \\PC12\Share. Contact your network administrator to request access.
When this error occurs, you need to:
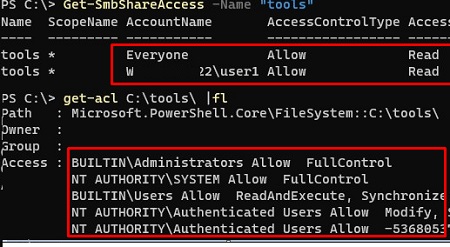
- Make sure that the user you are using to access the shared folder is granted access permissions on the remote share. Open up the properties of the shared folder on the server and brand sure your user has at least read permissions. Also, y'all can check the share permissions on the remote host using PowerShell:
Get-SmbShareAccess -Name "tools"
Then bank check the NTFS folder permissions:
go-acl C:\tools\ |flIf necessary, edit the permissions in the binder and/or share properties;
- Brand sure y'all are using the correct username and password to access the network folder. If you're not prompted for a username and countersign, try removing saved (cached) credentials for remote shares in Windows Credential Manager. Run the command
rundll32.exe keymgr.dll, KRShowKeyMgrand delete cached credentials for the remote computer you are trying to access.
The adjacent time you connect to the shared folder, you will be prompted for a username and password. Specify the credentials to access the network shared folder on the remote computer. You can save it in Credential Manager or add together information technology manually.
Other Fixes: Windows Cannot Access Shared Folders
This section provides additional ways to troubleshoot a problem opening network folders in Windows:
Source: http://woshub.com/cannot-access-smb-network-shares-windows-10-1709/
 If necessary, edit the permissions in the binder and/or share properties;
If necessary, edit the permissions in the binder and/or share properties;
0 Response to "Read Access Is Allowed From Event Dispatch Thread or Inside Read-action Only"
Enregistrer un commentaire